I’m a huge fan of Leo Laporte and TWiT. Lately, Laporte has been catching some heat on his shows for defending Google. In episode 237 of This Week in Google (TWiG), Leo and his panel discussed the growing animosity towards Google. In the most recent episode of TWiT, and reiterated on TWiG, Leo argues that Google is quite forward with their policies. You know that if you use Google products, they are using your information to target ads to you. The more they know about you, the more Google can provide you with a better experience.
Google knows where you are based on the GPS in your Android phone. Google knows what your voice sounds like from the “OK, Google” voice commands delivered via your phone or Glass. Google sifts through your GMail to pull out boarding passes for flights, appointment times so that Google Now can tell you when to leave based on location and traffic patterns, and even what you like to watch based on your YouTube viewing habits. All of this helps the former-search-now-everything giant better know you and deliver a genuinely unique experience when using their ecosystem.
To the end that Google seems to be quite transparent about what they do with your information, I completely agree with Laporte. However, the information isn’t why I feel Google is becoming more “evil” by the day. It is Google’s desire to control everything. Jeff Jarvis just rolled his eyes, but hear me out.
I don’t care if they want to buy Nest and know what the temperature is in my house. I don’t care if they can track me with GPS. I don’t care if they know what my emails say. Do I find it weird that one company wants to be in all of these different businesses? A little. But what concerns me most is Google’s refusal to play nice with other companies. I’m the 3% – I am a Windows Phone user. When Google planned to remove ActiveSync support from GMail was when I cut over to Outlook.com.
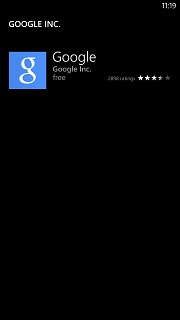
Google is slowly dragging you to their platform, as if their services aren’t enough. They are doing this by refusing to offer apps on other platforms. Don’t believe me? Look at the Windows Phone app store. See the picture above? The Google Search app is the ONLY app published by Google, Inc. I know, some of you are already asking “what’s the point of supporting Windows Phone?” But let’s be serious, rather than just ragging on a phone OS with small (but growing) market share. Why wouldn’t Google want their apps to be ubiquitous?
There is no GMail app. The phone can be configured to use IMAP and work quite well, but even Android itself separates the “Mail” app from the GMail app on their own Android platform. They offer a matching app on iOS. Why not offer a premium experience on any platform? Apple forcibly removed Google Maps from iOS, why not bring it to Windows Phone? Google has made the move to kill off support for 3rd party Google Voice apps, leaving those of us with MetroTalk out in the cold, despite not offering a full-featured solution on the Windows Phone platform.
Meanwhile, Microsoft offers a host of apps on Android. From OneDrive, to Office Mobile for Office 365, to Lync, to a full-featured Remote Desktop app, and a stand alone Bing app, for those interested. Even Xbox Music has made an appearance – but can I get Google Play Music for Windows Phone? No.
It isn’t what Google is doing with my data – I’d happily hand over more than they want to know! But I don’t have the option, unless I want to abandon my preferred user experience. There are a few of us crazies who like Windows Phone, and even Windows 8.1, how long is it until only Android and Chromebook users are allowed to access Google’s services? Google spent years making web-apps with the goal of being platform agnostic, but lately they seem to be creating a walled garden, with the sole intention of making outsiders jealous.
In this week’s TWiG, Gina Trapani agreed with Leo that there does seem to be a movement among “normal people” that Google is getting so big it’s scary. Leo thinks it may be a “drum beat” possibly relating to the fear of geek culture, as has been discussed before on his shows. But, in my experience, it’s the geeks leading this charge. Google might not be evil, yet, but their “don’t be evil” mantra can only help but become a whisper. As they dip their fingers in more and more industries, people are going to become increasingly cynical and wonder what their goals are. Their smartest move is to head users off at the pass and explain to the public what some more of their long term goals are for the company at large. It would put a lot of minds, including mine, at ease.